Published Nov 20, 2024
API Management: The Secure Phase
The secure phase of API lifecycle management focuses on protecting APIs through authentication, authorization, encryption, and access controls. It ensures that only the right users and systems can interact with an API—safeguarding data, maintaining compliance, and reducing the risk of misuse or breach.
As a core stage in full API lifecycle management, the secure phase plays a critical role in enforcing governance and trust, enabling organizations to scale APIs responsibly across teams, environments, and external partners.
The 4 phases of the API Management Lifecycle are:
This article discusses how Celigo API Management helps secure APIs with customizable plans and policies, ensuring compliance and mitigating risks when exposing services and data to users.
Security is critical in the world of APIs. Exposing services and data to internal and external users introduces risks that must be carefully managed. Celigo API Management empowers businesses to enforce top-tier security through customizable plans and policies, ensuring compliance with organizational standards.
The secure phase: API management video overview
Use case example:
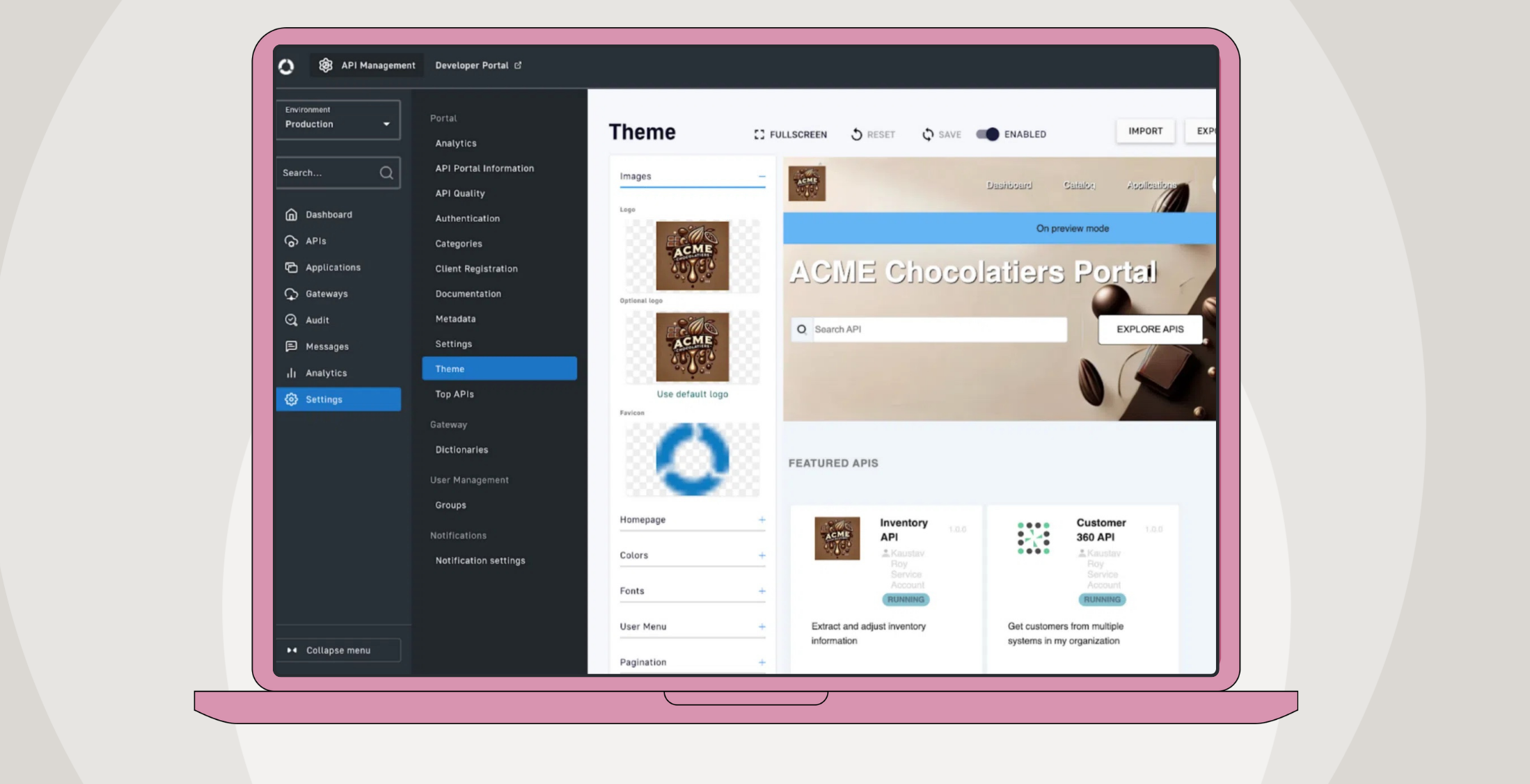
ACME Chocolatiers, an ecommerce company, can leverage Celigo to create APIs for managing inventory, processing orders, packaging, and shipping. These APIs would enable smooth interactions between external partners, customers, and their internal systems, facilitating a seamless digital transformation.
Managing API plans & subscriptions
Plans set the rules for how different users can access APIs. They act as access control, ensuring that only authorized consumers, such as internal users, external partners, or customers, can subscribe to and use the APIs. By creating different plans, companies like ACME can enforce security and governance measures based on the type of user, protecting sensitive data, such as customer details.

An application, such as a mobile or web app, needs to be added for each consumer to subscribe to one of the API plans published by ACME. The application can either be added by the API consumer in the Developer Portal or by the API publisher in the API console. Once subscribed, the plan controls the application’s access, ensuring it can only interact with ACME’s API as authorized.
There are four plan types: API key, JWT, OAuth2, and Keyless. At least one plan is required before an API can be deployed on the API gateway.
- API key: This plan is auto-configured when an API is pushed to API Management. After subscribing to an API key plan, an API key is generated, which is required to invoke the API. The consumer needs to invoke the API using the key name as “x-celigo-api-key” and the value as the API key.
- JWT: In case of a JWT or JSON Web Token plan, you need to select an algorithm, (e.g. HMAC_HS256 which is a 256 bit secret key shared by the API publisher and the consumer), followed by generating a secret key here, and entering the secret key in the Resolver parameter field. In order to subscribe to the JWT plan, you will need to enter the Client ID in the application. The JWT can be generated here by adding the “client_id” in the Payload and the secret key in the Verify Signature section.
- OAuth2: In case of an OAuth2 plan, you need to create a “Generic OAuth2 Authorization Server” resource. You need to add the Authorization server URL, which generates an authorization code when API consumer enters the credentials to login to the auth server, and the Token introspection endpoint, which introspects an incoming access token, from your own Identity provider, and also provide the Client Id, Client Secret of the client. Once the resource is created, you will need to create an OAuth 2.0 plan, and add that resource you created above, to subscribe to the plan. Once the subscription is accepted, the API consumer can invoke the API using OAuth 2.0.
- Keyless: This plan can be used only for testing purposes and is not recommended for securing the API.
Configuring API policies
Policies are a set of configurable rules that you would like to apply to the API request and response to manage aspects like security, governance, performance, and data transformation without modifying the backend API service.
There are 45+ policies that can be applied and enforced in Celigo API Management, and they can fall under one of the following categories: Security, Transformation, Performance, and Others.
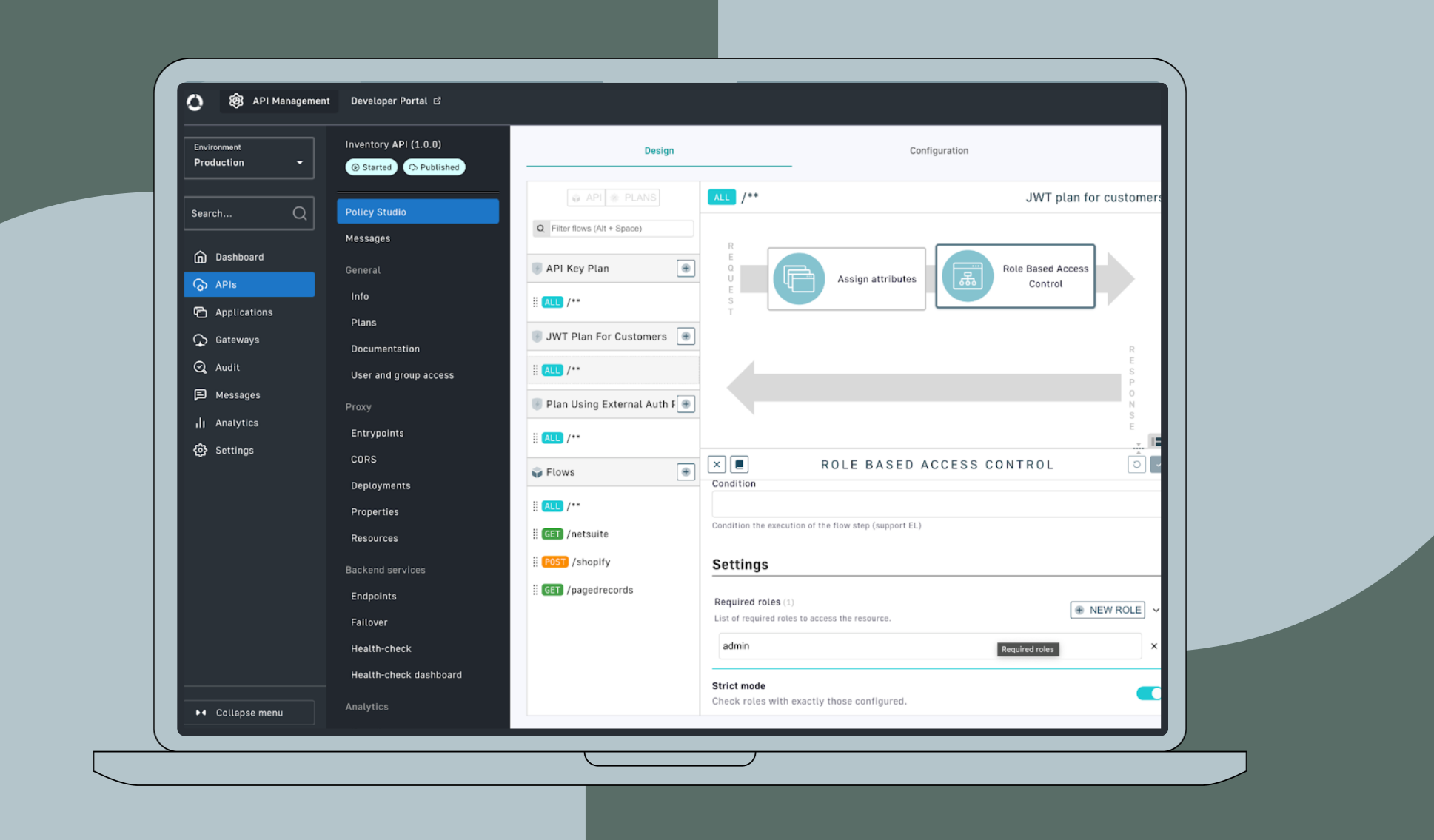
In the APIM console, the Policy Studio allows users to configure additional policies to enhance API security and governance. For example, ACME Chocolatiers might want to limit the number of API requests that external partners can make. By adding a Quota policy, you can restrict API consumers (e.g., partners) to a certain number of monthly API calls. If a partner exceeds this limit, the API gateway will block additional requests, returning an error response.

To further enhance security, ACME Chocolatiers can configure the Role-Based Access Control (RBAC) policy to restrict API access based on user roles. For instance, ACME might want only users with the “admin” role to be able to access APIs related to critical operations like order processing. With the RBAC policy, ACME’s API gateway checks the roles within the JWT claims and grants access only to authorized users.

Some other security policies that ACME can use are:
- IP filtering, which allows or denies API access to an IP address or a range of addresses
- Regex Threat Protection, which prevents SQL injection, and cross-site scripting attacks
- SSL enforcement, which allows access to requests with client certificate authentication.
- Data logging masking, which conceals sensitive data in the API logs.
Finally, Cross-Origin Resource Sharing (CORS) in the APIM console helps ACME Chocolatiers control which external domains can access their APIs. This prevents unauthorized third-party websites from interacting with ACME’s inventory or order management APIs, ensuring access to only trusted domains.
Building trust through API security
The Secure phase in Celigo API Management empowers organizations to confidently expose services to partners and customers while maintaining robust protection through customizable plans and policies. This level of security safeguards sensitive data and ensures compliance with industry standards, enabling businesses to build trust with their API consumers.
With Celigo API Management, organizations can safeguard their APIs with a security framework that acts as a digital fortress, ensuring that only authorized users gain access to critical data and services. By implementing these robust plans and policies, businesses can protect their operations while fostering secure, reliable collaboration with partners and customers.
Integration insights
Expand your knowledge on all things integration and automation. Discover expert guidance, tips, and best practices with these resources.